Information Security
- Basic Approach
- Declaration of Information Security
- Promotion System
- Major Initiatives
- Managing External Vendors and Suppliers
Basic Approach
In recent years, cyber attacks on the Internet have become more sophisticated on a global scale, and threats such as cyber terrorism using computer viruses, large-scale information leaks, and business email fraud are increasing.
As a corporate group responsible for the vital infrastructure of air transportation, our company has built an information security management system based on the ANA Group Information Security Management Rules Manual and we are routinely improving information system functions and taking security measures through defense in depth. The ANA Group's information security measures are based on the NIST-CSF (The National Institute of Standards and Technology Cybersecurity Framework).
Declaration of Information Security
ANA Holdings Inc. (hereafter "ANAHD") and companies which are linked with ANAHD through ANA Group management rules (hereafter "ANA Group") are fully aware of the importance of protecting information assets, including the personal information of customers. Therefore, ANAHD and ANA Group take the following measures to ensure compliance with relevant regulations and technical standards, handle such information assets accurately, safely, and appropriately according to the risks involved, and prove to be worthy of stakeholders' trust.
- ANA Group strives to ensure the confidentiality, integrity, and availability of the information assets in its possession.
- ANA Group will not disclose any information assets unless there are reasonable requirements to do so (requested by law, etc.).
- ANA Group establishes a special organization that addresses improvement of information security for the purpose of protection of information asset, provides as manual the measures to ensure information security and always makes efforts for maintenance and improvement of information security by means education, evaluation of effectiveness and audit of status of compliance.
- If any ANA Group executive or employee commits any act which impairs the confidentiality, integrity, and availability of any information asset, ANA Group will respond to such cases strictly according to established procedures.
Promotion System
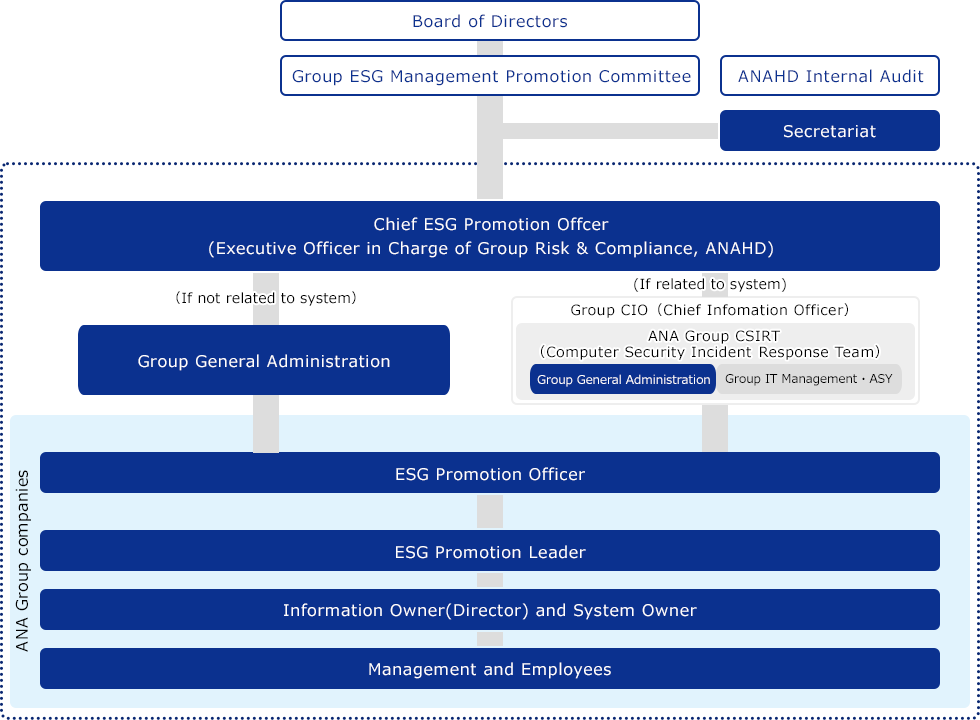
The Group ESG Management Promotion Committee monitors progress of measures in accordance with the ANA Group Information Security Declaration, which states the ANA Group's basic stance on information security.The Chief ESG Promotion Officer(CEPO) shall organize ANA Group information security and assume the role of chief executive officer for promotion of ANA information security. Each group company strives to ensure information security by having in place an ESG Promotion Officer (EPO) as responsible for promoting it and an ESG Promotion Leader (EPL) to actively promote it.
The Group IT Promotion Officer is the Chief Information Officer (CIO) of the ANA Group and provides technical advice in close cooperation with the CEPO, and compiles a quarterly 'Digital Governance Report', which is reported at regular meetings of the ANA Board of Directors.
Under the supervision of the CIO, the ANA Group CSIRT conducts activities aimed at preventing security events and early recovery in the event of an incident, and promotes the measures necessary to strengthen information security.
Incident response flow
Personal information is essential for providing ANA Group services, and we consider it an important asset entrusted to us from our customers. In the event of an incident involving information security, such as the data breach of personal information, it is reported to the Group General Administration Department through the ESG Promotion Leader of the department in charge. In the event of a serious incident, we will promptly establish a crisis response system as stipulated in the Crisis Management Manual and respond to emergencies in cooperation with related parties inside and outside the company. We established ANA Group CSIRT (Cyber Security Incident Response Team), a specialized team to respond to security issues, to ensure a timely response in the event of an incident.
![[Discovery/Notification] After recognizing the occurrence of an incident, the department in charge of the incident conducts fact-finding to understand the situation. The department then organizes the information, assesses the severity of the incident, and reports to the Group CSIRT. The Group CSIRT reports to the Chief ESG Promotion Officer and the Group IT officer. The Chief ESG Promotion Officer assesses corporate risks, while the Group IT officer assesses IT risks. [Triage] Upon receiving the report, the Group CSIRT considers triage support, coordination with external parties, and the necessity of external disclosure based on the received report. [Incident Response] The department in charge of the incident conducts an analysis of the incident, identifies the root cause and scope of impact, and establishes a response plan. The Group CSIRT confirms the effectiveness of the response plan and provides support such as revising the plan if necessary. The Chief ESG Promotion Officer and the Group IT officer collaborate closely to make decisions on response plan implementation, external disclosure, and provide instructions to the Group CSIRT. [Improvement/Prevention] Group CIRT and the department in charge of the incident will organize the remaining issues and manage medium- to long-term issues.](/group/en/csr/risk_management/security/image/image_02_2407.png)
Major Initiatives
Protection of Personal Information
In order to comply with national and international laws and regulations on the protection of personal data, the privacy policy and relevant internal rules are being modified, and the Amended Act on the Protection of Personal Information of Japan, as well as revisions to laws in other countries (e.g. the U.S., Europe, China, and Thailand) are being appropriately addressed. We also conduct in-house training to each employee on the importance of protecting personal information and the need for strict handling of such information. In April 2023, the Privacy Governance Team was established as a dedicated governance structure to strengthen privacy governance in order to realize business development based not only on strict legal compliance but also on ethical appropriateness in the future use of data, including platform businesses utilizing customer data assets.
Cybersecurity Measures
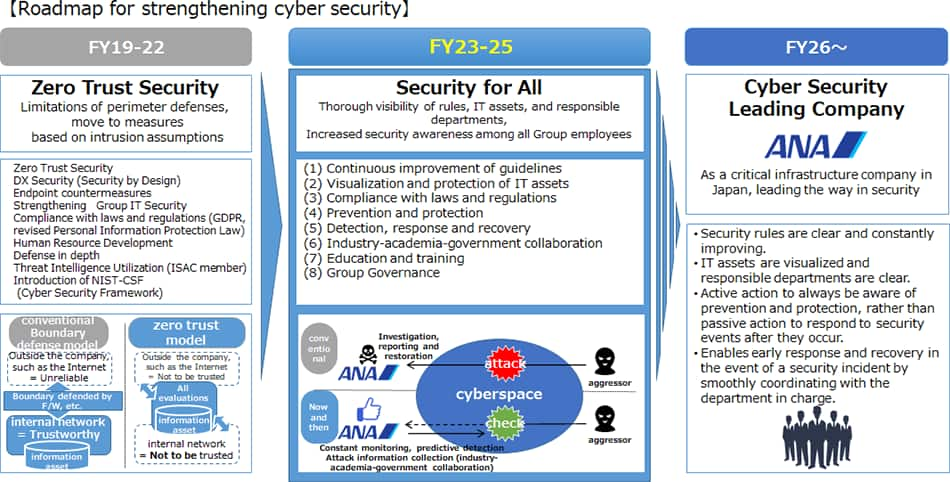
ANA is positioned as a critical infrastructure provider designated by various laws and regulations in Japan, and in accordance with guidelines set by relevant ministries, we implement multi-layered defense and monitor this defense 24 hours a day, 365 days a year. As cyberattacks become more sophisticated and cunning, the use of intelligence (early warning information on cyberattacks) is highly effective. We utilize it for preventive measures, including Aviation-ISAC (Information Sharing and Analysis Center), Transportation ISAC, and investigations into geopolitical risk information and the dark web. In terms of defense, we have also adopted the Zero-Trust concept, ensuring reliability by checking three points: "the person operating, the equipment generating communication, and the system processing."
Furthermore, in light of recent cybersecurity incidents at other companies, there is a growing need to strengthen not only ANA Group's security measures but also the defense capabilities across the entire supply chain. We are strengthening cooperation with relevant ministries, Keidanren (Japan Business Federation), and other related organizations, and through these organizations, we are undertaking necessary initiatives and collaborating in the dissemination of security enhancement awareness.
Meanwhile, within the ANA Group companies, which constitute a close-knit supply chain, we are addressing the visualization of each company's IT assets as a top priority. By managing the attack surfaces, which are external attack points in each group company, we prioritize discovered issues and vulnerabilities. We maintain close communication and consultation to ensure that each group company can take necessary countermeasures. We also strive to strengthen governance by utilizing the ANA Group IT Chart (a management document uniquely created by the ANA Group to grasp the IT usage status of each group company, such as OS versions of systems in use, whether security screening is conducted, software license expiry dates, etc.).
Through the "ANA Group CSIRT," which oversees the entire ANA Group, information sharing with relevant parties, including management, has been enhanced, and the speed of security incident triage and response has been improved.
Regarding security human resource development, we regularly post information security advisories and refresher training materials on the employee website. In addition to their daily duties, employees enhance their security awareness through "Plus Security" training.
On the other hand, the development of security specialists is an urgent issue. While continuing to hire experienced personnel, we are fostering security oversight personnel by encouraging them to attend specialized security training and participate in security community activities involving other companies. For legal compliance, we are progressively addressing privacy laws and regulations in each country. Domestically, we are promoting various IT system and cybersecurity measures required by the Economic Security Promotion Act through close collaboration with the government, Keidanren, and other relevant organizations.
Implementation of Education and Training
In order to understand the importance of information security, including the protection of personal information, and the threat of cyber attacks, and to ensure that actions are taken to protect information assets, we have established a permanent e-learning system for Group employees and regularly provide them with knowledge that incorporates the latest examples.In the IT sector, CSIRT training is conducted monthly as training in preparation for security incidents, while training for management and relevant departments is conducted at least once a year.
Implementation of Information Security Risk Assessment
The ANA Group regularly conducts information security risk assessments at its domestic and international business sites using specialized teams. Through these assessments, we inspect the management status of information assets from a third-party perspective, identify challenges, and work towards improvements. In addition, we have established an annual self-assessment system to review compliance with regulations, striving to enhance information security across all organizations. Furthermore, we endeavor to reduce risks by conducting regular vulnerability assessments and penetration tests. For key systems, these are performed quarterly. Moreover, in certain business areas, we obtainin PCI DSS compliance certification and ISO27001 certification through external audits.
Managing External Vendors and Suppliers
To maintain information security and personal data protection standards, the ANA Group Information Security Management Manual establishes selection criteria for contractors and required clauses for contracts, along with ongoing oversight.